Instead of trying to make passwords stronger, it’s time for your business to start getting rid of them altogether.
Everyone knows that passwords are inherently vulnerable to cybersecurity threats. That’s why you’re constantly urged to use multi-factor authentication (MFA), which until recently meant adding a layer or more of protection to your passwords. But in recent years, the growing diversity and availability of alternative authentication methods have made it so that you, as a business leader, can begin implementing MFA without passwords.
Our recent 2022 Passwordless Authentication Survey found that 82% of business leaders are ready to adopt passwordless methods. So let’s talk about how your business can start boosting its security by ditching passwords—even if it’s only a portion of them.
Key survey findings
1. The vast majority of business leaders (82%) are willing to adopt passwordless authentication methods.
2. The most popular authentication method (43%) is to use something you know (e.g, passcode), but using something you are (e.g., fingerprint) is only a few percentage points behind (38%).
3. Most businesses (56%) are now required by regulation to use multi-factor authentication and a significant portion (17%) must use it to comply with a cyber insurance policy.
Passwords cause friction for users, leading to even weaker security
For a password to be worth anything, it must be strong. In 2022, that means at least twelve characters including a mix of numbers, special characters, and both upper and lowercase letters. And be sure to use a unique password for each and every account. Oh, and you should change them regularly. If you forget a password, just go through a convoluted process to create a new one or sit on hold with the help desk.
In other words, passwords offer a poor user experience—which is why most users don’t bother following basic password protocols.
An alarming 77% of our respondents use the same password for multiple accounts at least some of the time—nearly half (46%) of that percentage admit to reusing passwords often. This is a serious problem because password reuse is a primary driver of account takeover attacks and data breaches. When asked how they remember their passwords, 26% write them down on paper, 25% store them in an online document, and 21% use personally meaningful information.
Passwords offer relatively weak security in the best circumstances, but as our research shows, many users leave themselves (and their company) nearly defenseless. This makes your company vulnerable to phishing schemes, keyloggers, brute-force attacks, and any number of other tactics cybercriminals use to defeat passwords.
So what exactly is passwordless authentication?
It’s exactly what it sounds like—authentication without the use of passwords. But it’s not that simple. You can’t call someone up and say “I’d like to order some passwordless authentication.” Don’t think of passwordless as a destination—think of it as a goal, and any progress you make toward your goal of getting rid of passwords makes your company more secure.
Before we go any further, let’s break down the alternatives and what people think about them. There are three fundamental types of authentication:
Something you know, such as a pattern or a PIN code
Something you are (or do), such as your face or fingerprint
Something you have, such as your mobile device or a USB key
Today, more than two in five people (43%) still prefer to use something they know–this isn’t surprising since the use of passwords, PINs, and security questions have been the most common authentication methods for decades. What might be surprising is that more than one in three (38%) prefer to use something they are, also known as biometric authentication. Rounding out our results, about one in five (19%) prefer to use something they have.

Consider these preferences as we dig into password alternatives and the options that might work best for employees at your company.
Improve security by adopting passwordless authentication
If passwordless authentication can improve security, would you be willing to make the switch? We posed this question to 389 business leaders, and a full 82% said yes. And while passwordless authentication can be performed as a single-factor (e.g., use your fingerprint to unlock your phone), businesses must use MFA to protect access to critical systems and sensitive data.

Fortunately, nearly all business leaders (95%) say their company uses MFA for at least some business applications—55% say they use it for all applications. Those numbers have been climbing steadily over the years that we’ve been asking that question. One reason is that MFA isn’t just best practice, it’s increasingly required. More than half (56%) of the business leaders we surveyed say their company is required to use MFA by regulation (e.g., HIPAA, PCI DSS, SOX), and 17% are required to do so by a cyber insurance policy.
With all of that in mind, let’s take a look at how passwordless MFA works.
Enable passwordless MFA with authentication tokens
An authentication token is a hardware device (or data object) that is connected with a person’s identity to enable access to digital assets. The token, typically a smartphone or USB hardware key, is assumed to be in personal possession of the identity to which it is bound.
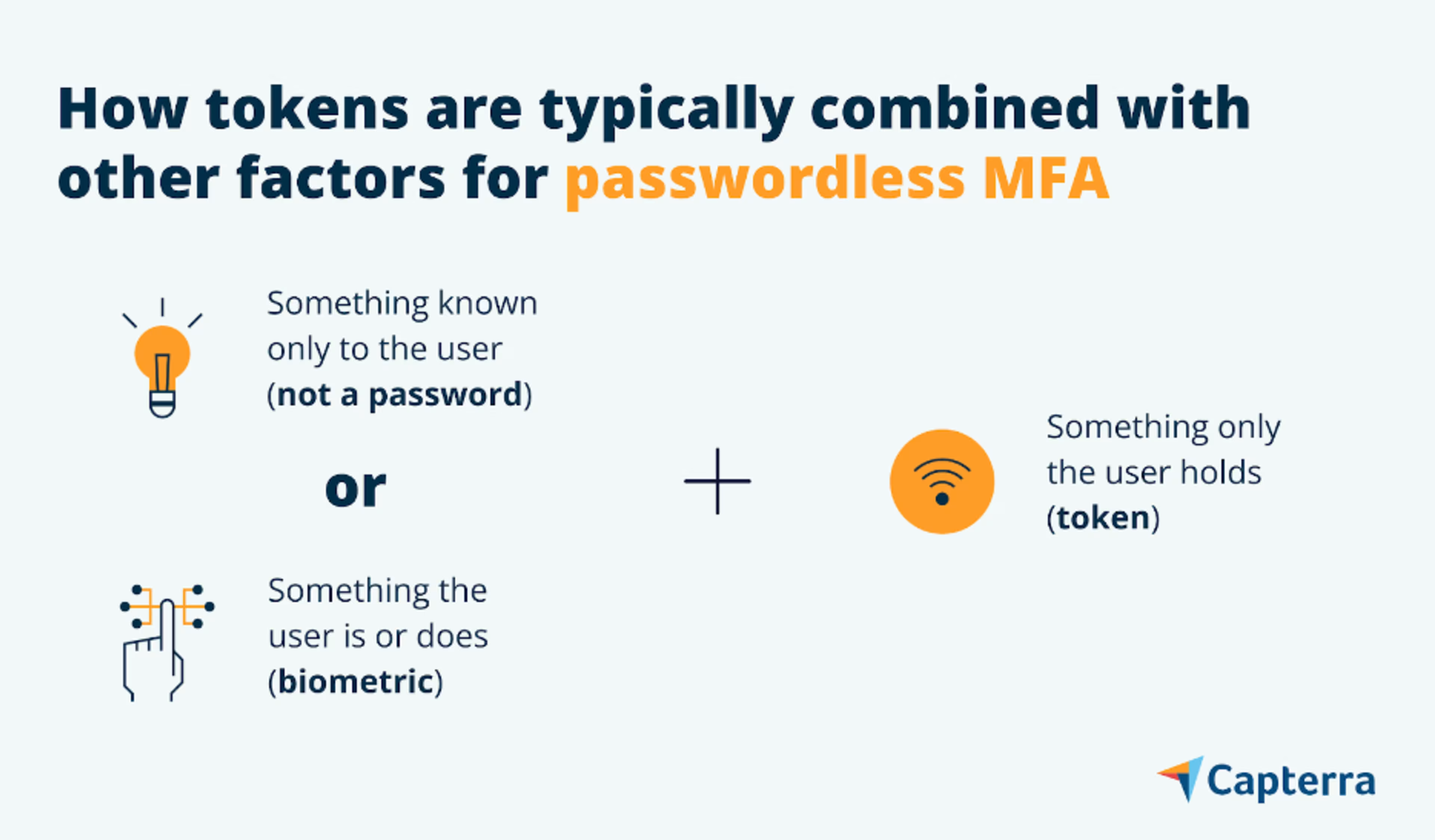
Phone-as-a-token has been around for many years and comprises out-of-band (OOB), one time password (OTP), and increasingly, QR code authentication. Recently, public-key tokens have been gaining ground and could very well be the future of token-based authentication. Let’s take a look at how these different types of tokens are used.
Out-of-band (OOB) authentication
Some OOB methods send a code to your email or simply send a “magic link” that you can click to gain instant access to the service. It’s worth noting that the use of email and magic links within a passwordless scheme is questionable because most people use a password to access the email account from which they receive their one-time password or link.
OOB authentication is designed to use two different channels for authentication, such as an internet connection and a wireless network. A common example of OOB authentication is when you receive an SMS message or automated voice call on your phone with a code that you then enter into a website. Other methods include push notifications that are more secure than SMS messages.
One-time password (OTP) authentication
OTP authentication is generally performed using an authentication app on a mobile phone (although hardware OTP devices do exist) to generate a temporary code, which is then entered to gain access to a digital asset.
Quick response (QR) codes
QR codes are everywhere from restaurants to Super Bowl ads, and increasingly, they’re being used for security purposes. By using a smartphone to scan a QR code displayed in a website’s login pane, you can be authenticated. Of course, the drawback is that QR codes can’t be used to gain access to a site from the phone itself.
Public-key tokens
Public-key tokens authenticate using asymmetric cryptography (i.e., a public and private key pair) and often use an X.509 certificate. Public-key tokens can be software-based or hardware-based including USB hardware keys, smartcards, and bluetooth or NFC-enabled smartphones and wearables.
Perhaps the future of passwordless authentication, Fast Identity Online (FIDO) is a set of protocols that incorporates public-key tokens and is specifically designed to reduce reliance on passwords. FIDO authentication uses two steps, one to unlock the authenticator and the next to generate cryptographic keys needed for authentication with an online service.
The factor used in the first step, to unlock on the local device, can be selected from whatever option is available, such as a fingerprint, entering a PIN, or inserting a dedicated hardware device (e.g., YubiKey). After unlocking the FIDO authenticator, the device supplies the correct private key that corresponds with the service provider’s public key. The information provided in the first step remains private, never leaving the user’s device.
Authenticating with something you know (but not a password!), something you are, and everything else
Passwordless authentication can use something you know, so long as it’s not a password. The most common alternative is a PIN. And while a PIN might seem similar to a password, it’s quite different. PINs are typically used to unlock a local device, such as a debit card. Without a PIN, your bank card is useless. Conversely, passwords are matched to information stored in a central database and are vulnerable in and of themselves.
Other common methods in this realm include picture and pattern recognition. During registration, some services will ask you to select a picture. Then, when authenticating, you select your picture from several options. Similarly, pattern recognition authentication requires you to remember preselected points on a picture or a grid.
Biometric authentication becomes more accepted
Biometric authentication uses unique physical characteristics, such as your face or fingerprint, to authenticate your identity. Biometric technology is becoming mainstream, especially when used for security purposes. Our survey finds that 76% of consumers are comfortable using facial recognition to access their computer or phone. Perhaps more surprisingly, 64% are comfortable using it to log-in to an online account.
Biometrics authentication is rapidly integrating with phone-as-a-token methods. Smartphones have microphones, cameras, and fingerprint scanners, all of which can be used to support an array of biometric authentication modes that simultaneously confirm possession of the device.
Contextual authentication offers flexibility for passwordless users
Beyond actively confirming your identity, contextual authentication methods passively detect risk using factors such as location, activity, and device identifiers. Also known as signals-based authentication, this process may allow the ultimate passwordless scenario known as zero-factor authentication (0FA), whereby the user is granted access if no risk signals are present. If the system is unsure, the user is simply prompted for an authentication measure such as a PIN or biometric trait.
Advanced models such as continuous adaptive trust (CAT) use machine learning to analyze even richer sets of variables about the user to determine risk, such as measuring keystroke pressure or recognizing a user’s specific movement when walking with a device.
Three steps you can take to implement passwordless authentication
As mentioned, passwordless is aspirational (at least for now), and every step you take toward it boosts your overall security posture. In that spirit, let’s take a look at three steps you can take to begin reducing the number of passwords at your company.
1. Collaborate with stakeholders to identify priorities and preferences
Gain buy-in from key stakeholders by explaining exactly how moving away from passwords will benefit their teams and make their jobs easier. Determine priorities for security improvements, learn how workflows might be impacted, and identify preferences for new authentication methods.
2. Optimize existing tools that allow for passwordless methods
Take stock of and exploit passwordless options that you already have at your disposal. For example, if your business already uses Windows 10, you can use Windows Hello for Business which combines a local authentication method, such as biometric or device-based authentication.
Ask the following questions:
What passwordless options do we already have available?
Can we modify current authentication flows to avoid passwords?
Will these changes ultimately reduce friction for users?
3. Shift future investments toward passwordless-ready tools
To prepare your company for the universal adoption of passwordless authentication, it’s important to simplify your migration path over time by shifting current and future investments where possible. When procuring new software, consider the availability of authentication options that leverage biometrics, phone-as-a-token, and emerging protocols such as FIDO2.

Our reliance on passwords will soon pass
We’ll eventually arrive at a future where you won’t need to remember a password, servers don’t have to store them, and hackers can’t exploit them. That is a much more secure digital world than the one we live in today. But it will happen little by little and will require new ways of thinking about security, such as zero-knowledge proofs and zero-trust security models (both of which we’ll be diving into during upcoming research reports).
The trend is to move away from passwords and toward more personal, contextual, and frictionless forms of authentication.
Want to learn more about protecting your business? Read our recent article: 8 Ways To Protect Your Small Business From Cyberattacks
